o, You forgot your password. I am here to help you just at the instant you asked for help. I will explain the process in my style.First the main concept and then its implimention. This way, I can force you to read all the content and upgrade your knowledge level somewhat.  .
.
“I am telling you for the educational purpose only. Use it at own risk. I am not responsible for any harm done by you to yourself and others.”
Lets gets ON.
If you have used Linux , you will know that there are two kinds of users in the Linux OS. First one is a simple user that has permission to perform normal routine work on the computer system on which he has access. And second one is root. The root has all sorts of permissions you can think of.
Same is the case for Windows. We too have two kinds of users in Windows, one is User( having normal Administrative privileges) and other one is Administrator. We think that the Administrator has all the power in his hand, and we can do anything with this account. However, it is not true. Administrator does not holds the total power. If you are a keen observer and somewhat experimental in nature, you must have noticed in Windows Xp, that some processes that are triggered by the owner System can not be ended by the Administrator himself.
So, I think you got the real player behind the game.
Administrator is the user account that certainly has got more administrative powers than the normal user but do not have all. It is a sort of power user. In Windows XP, mostly all the users do not temper with this Administrative account, so it is easy to press Ctrl+Alt+Del key on the Login Window, and then writing the Administrative in the User field and then hitting the Enter key and by doing this, you got entrance to the Administrator account and now, you can remove the password of the victim.
But, you can’t do this in Windows 7, you do not get that login user and pass window here, and even in the case of Windows XP, if original and genuine user has applied the password in all the available accounts and Administrator, you would have been choked there.
Till now, I told you about the root user of Windows and one old trick of breaking Windows XP password.
Windows employs File Protection System. This protection is mostly responsible for keeping you in limits as decided by your authorized level. So, it simply means that if you want to have a date with SAM files, you will have to get rid of the FPS. It is not an easy task because FPS get switched on at the moment you see your login screen. So, it simply means that you need to do anything you want when Window is not running, I mean when there is another OS on your computer.
Linux Live CDs would come to you to rescue you. They will give you a live demo how the Linux machine looks like. You won’t need to install the Linux in your HDD.
Well, before I tell you about the actual procedure, I would like to tell you about the methods I tried to get rid of password. I tried 4 methods. Fourth one is the universal method that I got.
1) Firstly,, I thought renaming the SAM file located in C:\Windows\System32\Config folder . On some in depth reading and researching I found that this method only works for the Windows XP SP1. If you did it in after Windows of XP SP1, you will be welcomed by a Warning message that declaring that SAM file is corrupted then you computer will reboot. If you do it Windows 7, you will not be fortunate enough to know what the hell has happened to your computer. Your computer will keep on rebooting in the boot screen.
2) Secondly, I thought that I should replace the while config folder files of target computer with the my config folder ( that do not has password). This method will work, if you have the two systems of same architecture and same configuration. And if you do not have that, you will welcomed by BSoD. (Blue Screen of Death).
3) Another alternative could have been copying all the SAM, SYSTEM files from the Repair folder in the C:\Windows\Repair. This method will work if this folder existed in your computer. I mean it does not exists in Windows 7. But it is there in Windows XP Later 2 Service Packs (2 & 3). It will take to your computer’s ICE AGE. I mean you will have no drivers installed and no software. But certainly, it would work. 
4) In the 4th and final method, I tried, I used Linux Live Cd and got into Windows File System.
Let me explain everything with the help of screen shots.
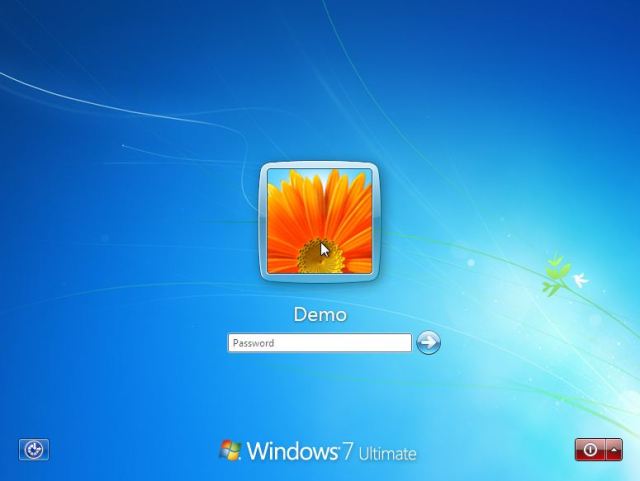
This picture shows that I really got a computer that has an Windows 7 where I forgot the password intentionally to write the post  .
.
You need to have a Linux Live Cd. I am using Virtual Box for demonstrating the breaking. However, today most of the motherboards support booting from pen drive, so it would be fine if you could just make a pen drive boot-able and try the Linux live CD from that only.
So, I booted into Linux, this screenshots shows the options you need to choose to go on. Hit trying the Ubuntu. Then, you will see the desktop of the Ubuntu after you got into that.
And the Desktop looks like.
After this, Click on the Tool Bar option “Places”. A drop down menu would come up in which you are required to select the computer option. You can select any other option too. The Computer options leads you to a window like
I am showing you this on the Virtual Box. So, I have made just one partition of size 11 GB. You would have to recognize the correct partition of Windows, C Drive. It could be done simply by opening each partition and examining the Files and Folders in the partitions.
I opened the partition and I got the files.
As you can see, I got Windows folder here. It is the System Root Drive. C Drive. Now, firstly nevigate to C:\Windows\System32 Folder. And locate the file Sethc.exe. Right click on the file after selecting it. Go to other location in your computer. Anywhere. Right CLick and create a new folder. Copy this file here (sethc.exe). Now, Locate the CMD.exe file and copy to it another location and rename it to sethc.exe and place it in the C:\Windows\System32. Now, you can exit Linux Live Cd now. I hope you will be able to do copy paste by yourself.
So, After you have done this. Restart your computer. If you used Cd drive. remove the Cd, if you used Pen Drive, remove your pen drive. Now, again you will see the same login screen asking for password.:(
However, if you press Shift Key for 5 times, or hold it for nearly 8 seconds, A change would happen. Let us see what will happen.
The Command Prompt that appears here is very very special. 1st reason is that it is not annoying me for Password. Secondly, it is running at the supreme user mode available in Windows.
If you want to know it. Just type “whoami”. It will tell you who he is.
The main point is to remove the password. It is most simple. Just type
net user username *
and press enter 2 times or enter the new passowrd. Passowrd would be reset. Here, username stands for the your Username which is in our case is Demo. Anothere thing to be seen is, there is a space between the username and *.
You can exit the cmd by exit cmd. And if you have not entered any password, then do not type anything into the passowrd field, only press enter. You will be forwarded to Desktop.
Now, time for some explanation. Sethc.exe process is responisble for two type of keys. Sticky keys and filter keys. I have replaced the sethc.exe with the command prompt. Sp, when the system call tries to invoke sethc.exe process, it calls the Cmd. Since, no user has been login still, the command prompt uses a account which is always login. System the mot powerfual account in Windows 7. Through this Cmd, you hold all the power to do anything to this computer and hence, you changed the password.
You can use this method on Windows Xp. Only thing that would not work in XP is whoami command. Everthing else would be same as above.